How the Tor Browser Works: The Technology Of Onion Routing
|
|
⌛ Time to read 5 min
Shipping Worldwide 🛩️
Call Us: +357 97729099 📞
WhatsApp Us: +357 97729099 🔔
Email: info@cybershopcyprus.com 📧
Follow Us On Social Media ✌️


✍️ Written by: Nearchos Nearchou
|
📅
|
⌛ Time to read 5 min
In a digital age where data is more valuable than oil, internet privacy is a growing concern. From governments and advertisers to hackers and surveillance systems, there’s an ever-increasing interest in monitoring what you do online. That’s where the Tor Browser comes in—a powerful tool that helps you stay anonymous, access blocked content, and protect your online freedom.
In this article, we’ll explore how the Tor Browser works, the technology that powers it, its benefits and limitations, and how you can use it safely—especially if you’re located in Cyprus or any region with growing interest in privacy.
The Tor Browser is a free, open-source web browser specifically designed to enable anonymous communication on the internet. It routes your web traffic through a decentralized network of volunteer-operated servers, masking your location and protecting you from surveillance and tracking.
Developed by the Tor Project, a nonprofit organization, Tor (short for The Onion Router) uses multiple layers of encryption and relays to hide your IP address, identity, and online activity. Think of it as a privacy-first version of Firefox on steroids.
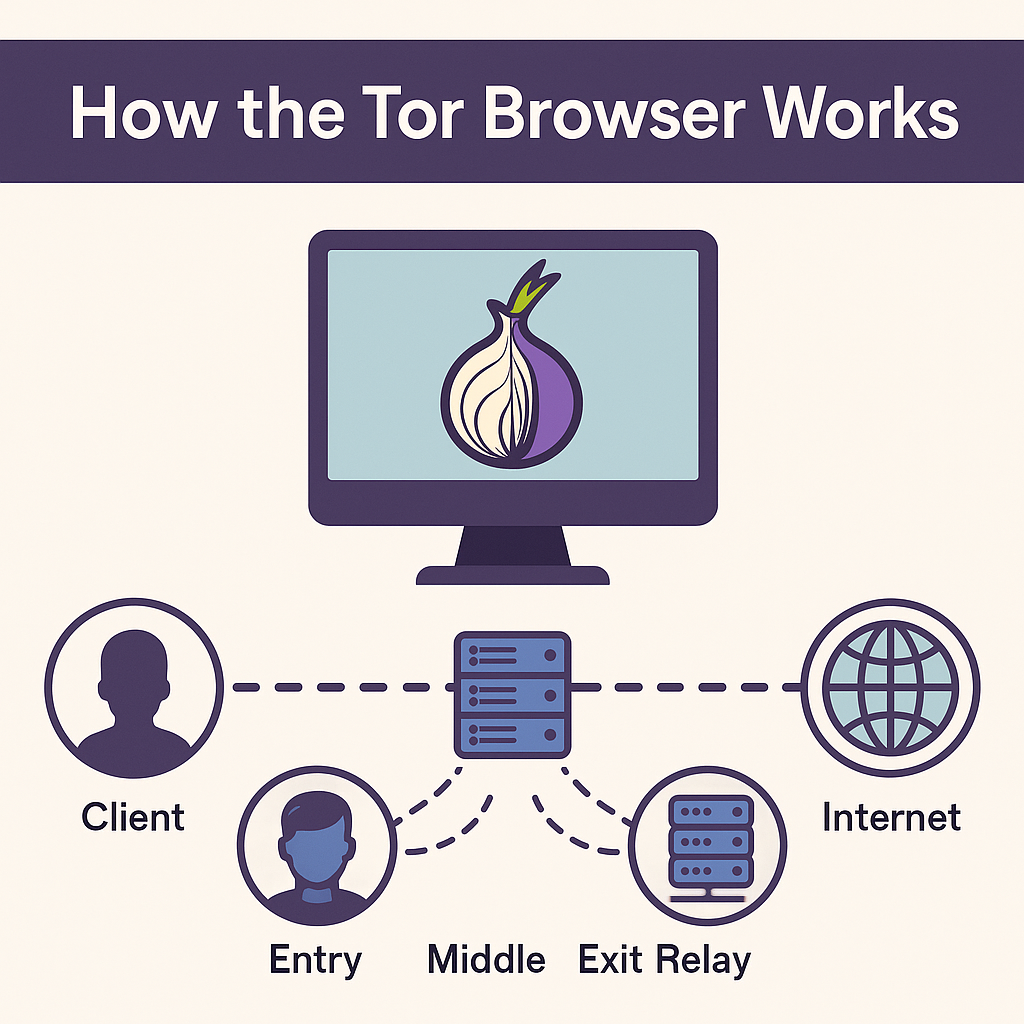
At the core of Tor's technology is onion routing —a technique that encrypts data in multiple layers and routes it through several servers (called relays). This method ensures that no single relay knows both who you are and what you're doing.
Your request is encrypted in layers —like an onion.
The encrypted data is routed through three Tor nodes:
Entry (Guard) Node – Knows your IP address, but not your destination.
Middle Node – Passes encrypted data, knows nothing about origin or final target.
Exit Node – Decrypts the final layer and forwards your request to the website, but doesn't know who you are.
Each node decrypts just one layer, forwarding the remaining encrypted data to the next node.
The website receives the request, but only sees the exit node’s IP, not yours.
✅ Result: Your identity and location remain hidden, even from the sites you visit and your ISP.
| Feature | Tor Browser |
Chrome / Safari / Edge |
| IP Masking |
Yes | No |
| Traffic Encryption |
Multi-layered via Tor | HTTPS only |
| Anti-Tracking |
Built-in | Add-ons required |
| Access .onion sites |
Yes | No |
| Privacy Focus |
High | Low to Medium |
| Script Blocking |
NoScript pre-installed | No native protection |
The .onion domains are special websites that are only accessible via the Tor Browser. These sites exist within the Tor hidden services layer of the internet—commonly referred to as the dark web.
ProtonMail (Secure Email): protonirockerxow.onion
DuckDuckGo (Private Search): duckduckgogg42xjoc72x3sjasowoarfbgcmvfimaftt6twagswzczad.onion
New York Times : https://www.nytimes3xbfgragh.onion/
⚠️ Note : While many .onion sites are used for legitimate privacy-related purposes, others may be involved in illegal activity. Use caution.
When you download Tor Browser, you get much more than just a browser:
Tor Daemon: The core engine that connects to and routes traffic through the Tor network.
Torbutton: A Firefox extension that controls privacy settings.
NoScript: Prevents scripts and plugins (like JavaScript) from running without your consent.
HTTPS Everywhere: Forces encrypted connections where possible.
Tor Launcher: Helps establish your Tor connection securely.
You can use Tor on mobile via:
Tor Browser for Android – Official and recommended.
Onion Browser for iOS – Community-supported but functional.
Orbot – A Tor proxy for Android that routes all traffic through Tor.
Yes, Tor is 100% legal in Cyprus. You can download, install, and use it without restrictions. Tor is a tool, not a crime.
However, using Tor to access or participate in illegal activities (e.g., buying illegal goods on dark marketplaces) is still illegal and punishable under Cypriot and EU law.
User Type |
Purpose |
| Journalists | Protect sources and communicate securely |
| Whistleblowers | Leak confidential info anonymously |
| Activists | Bypass censorship and government surveillance |
| Researchers | Analyze darknet data and monitor illicit networks |
| Everyday Users |
Avoid ads, trackers, and protect their digital footprint |
To make the most of Tor’s protection, follow these essential guidelines:
Keep Tor Browser updated.
Stick to HTTPS sites.
Use Tor Bridges if Tor is blocked in your region.
Use Tails OS (a privacy-focused operating system) for maximum anonymity.
Logging into personal accounts like Gmail or Facebook.
Downloading and opening files (PDFs, Word docs) outside of Tor.
Torrenting through Tor (it's not designed for P2P and exposes you).
Resizing your browser window—it may reveal your device’s screen size.
Tor’s multi-hop routing naturally makes it slower than regular internet browsing. Every request must pass through at least three different servers, often located in different countries. While this may not be ideal for streaming or gaming, it's a tradeoff for privacy and anonymity.
|
Myth |
Truth |
| “Tor is illegal” |
False – Using Tor is legal in most countries, including Cyprus. |
| “Only criminals use Tor” |
False – Tor is used by millions, including journalists and activists. |
| “Tor makes you invincible” |
False – Tor boosts anonymity, but it’s not foolproof if used carelessly. |
Tor is a neutral tool. It empowers those fighting for freedom, human rights, and journalism—but it can also be misused. The Tor Project strongly discourages illegal use and focuses on defending the rights of ordinary people to privacy and freedom of information.
The Tor Browser is one of the most powerful tools available for online anonymity and digital freedom. Whether you're avoiding tracking, accessing censored information, or conducting private research, Tor provides a secure and decentralized way to stay hidden online.
In a world where your data is constantly collected and exploited, using the Tor Browser is more than just a technical decision—it’s a stand for your digital rights.
Looking to take your privacy even further? Check out our curated cybersecurity gear:
🔐 Encrypted USB drives
📱 Faraday phone cases
🧳 RFID-blocking wallets
📘 Privacy guides and books
Nearchos Nearchou
Nearchos Nearchou is a determined person and 1st Class BSc (Hons) Computer Science and MSc Cyber Security graduate. He is a big tech-lover and spent several years exploring new innovations in the IT field. Driven by his passion for learning, he is pursuing a career in the Cyber Security world. Passionate about learning new skills and information that can be used for further personal and career development. Finally, he is the author of the book “Combating Crime On The Dark Web”.
📬 Subscribe to Our Newsletter
Stay updated with the latest tech insights.
Tax included.
| Price |
|---|
| SKU |
| Rating |
| Discount |
| Vendor |
| Tags |
| Weight |
| Stock |
| Short Description |
Description here
Description here


